Implementing Channels in TAK
Change Log
20230826 - Added iTAK
20241014 - Removed the requirement for channels.zip and Device Profiles
So, you want to implement channels? First, let's define channel and group usage within TAK. Honestly, they both are the same. The difference is groups are active 100% of the time they are applied. For example, if you're a member of multiple groups you participate in those groups no matter what. With channels, you can enable the groups you need at any time. If you need a refresher on groups, click here.
If you recall with the TAK Server there is a flat-file authentication method, by default is the way you manage users and groups out of the box. The other method is the lightweight directory access protocol (LDAP) or Microsoft Active Directory (ADS). Channels can be applied to both authentication methods and are controlled by the end-user or client at any time. When utilizing LDAP/ADS the group or channel being applied to the end-user or client is matched against the certificate's common name or subject. It's important to note that when using external certificate authorities (CA) for issuing certificates the common name matches the LDAP/ADS authenticated username. To learn more or implement client LDAP/ADS authentication using certificates click here.
Configuring the TAK Server
Channels are not enabled by default. First, edit our core configuration file to accept the channel configuration by adding the x509useGroupCache attribute to the auth element of the CoreConfig.xml and setting it to true. To edit the CoreConfig.xml start by accessing your TAK Server either via a remote connection or by direct access. Once authenticated to your TAK Server navigate to the /opt/tak directory. Then we need to invoke the tak user and edit the CoreConfig.xml.
# Change directory to /opt/tak
cd /opt/tak
# Change user to tak
sudo su tak
# Edit the CoreConfig.xml
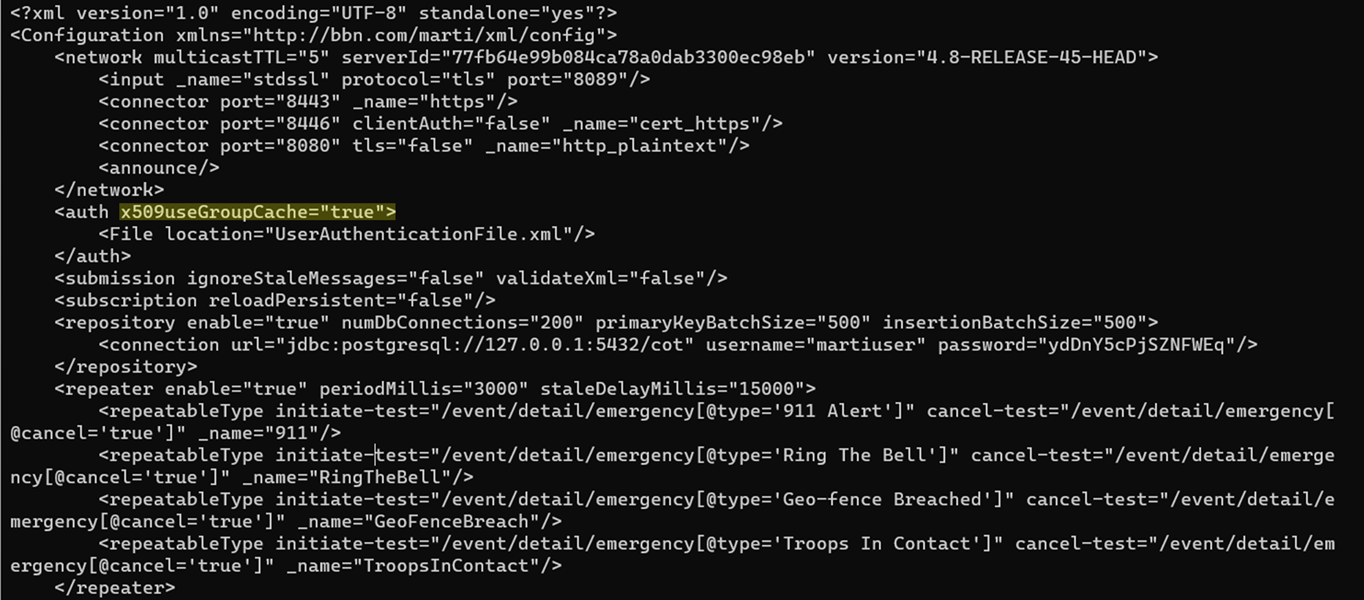
vi CoreConfig.xmlWithin the CoreConfig.xml navigate down to the auth element then add the x509useGroupCache attribute and set its value to true.
<auth x509useGroupCache="true">
<File location="UserAuthenticationFile.xml"/>
</auth>Enable Channel Support within the CoreConfig.xml
As always, after we edit the CoreConfig.xml we must restart the takserver service.
# Exit tak user
exit
# Restart the TAK Server service
sudo systemctl restart takserverRestarting the TAK Server service
Selecting Active Channel
Channels are only available for clients that are using certificate auto-enrollment. Clients utilizing the hard certificate - those generated by the makeCert.sh will not have active channels available.
WinTAK
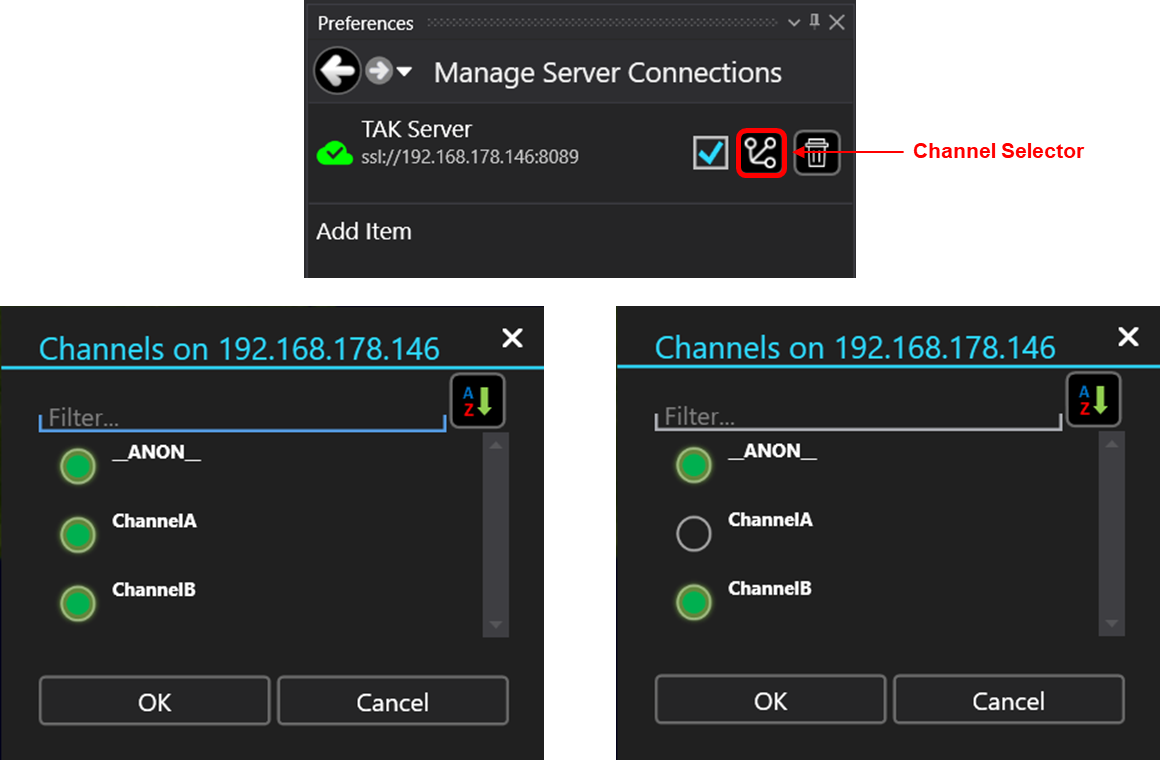
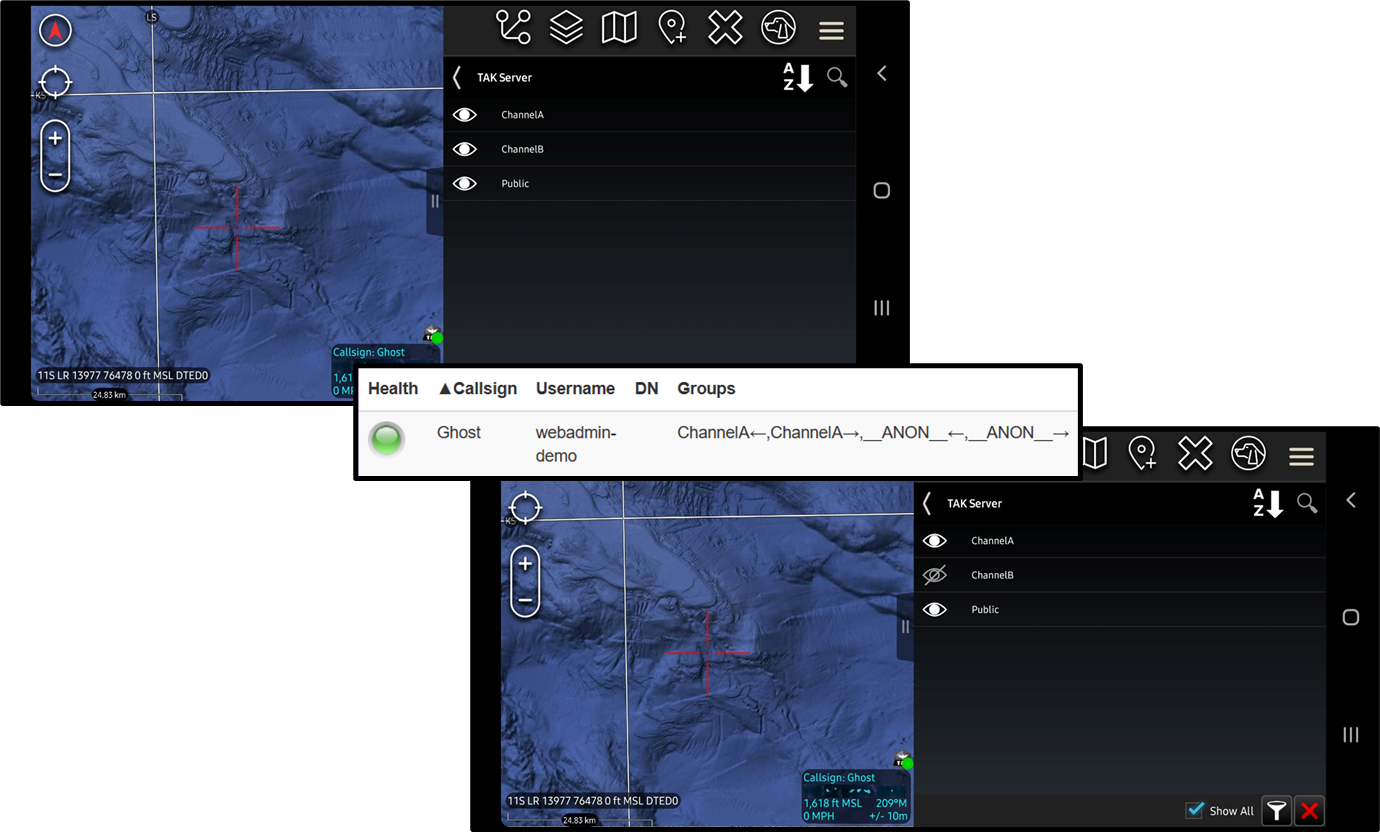
Within WinTAK that Channel selector icon is placed in the Manage Server Connections menu dock. When you click on this icon it will display which groups the client is participating in actively. This is identified by the filled-in green dot. To remove participation from a group but maintain access simply click on the green dot to toggle it on or off.
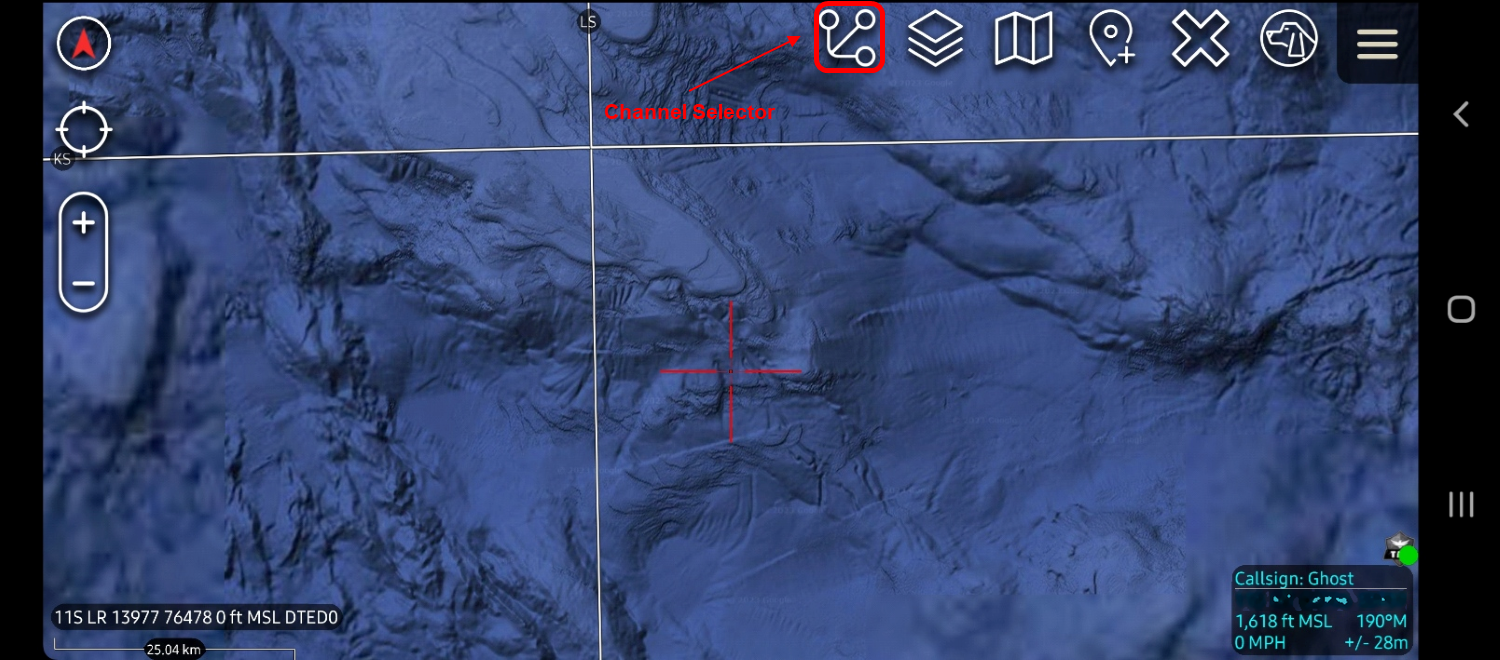
ATAK
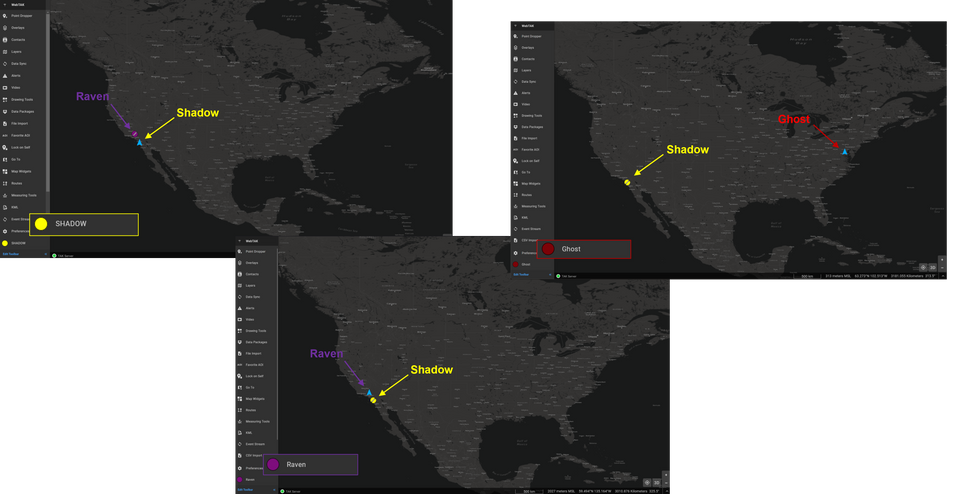
Within ATAK (version 4.7+) the Channel selector now shows up in the top menu bar. Similar to WinTAK when you click on this icon it will display the active groups that ATAK is participating in. Simply toggle the group you wish to participate on, or off which will remove access to the group but will not delete you administratively. Within the Client Monitoring Dashboard within the TAK Server, we can see that Ghost (ATAK) is participating in the ANON and ChannelA groups but is inactive in ChannelB.
iTAK
iTAK works with Channels as well, I just don't have an iPhone to test. I will update this portion when I can. Just know Channels are supported in iTAK as well.
Conclusion
Groups and Channels provide a powerful enhancement from the traditional deployment of Groups within the TAK Server. It allows the client the freedom to actively select the Group they wish to participate in without having the TAK Server Administrator move users in and out of Groups. This can be extremely helpful if you have multiple Groups applied but need to maintain access but want to turn the other Groups off.

